Your Ultimate Hookup Resource
Explore a comprehensive directory for connections and relationships.
Mobile Security: Are You Really Safe in Your Pocket?
Uncover the shocking truths about mobile security and how safe your data really is! Don't let threats hide in your pocket—read more now!
Top 5 Mobile Security Threats You Need to Know About
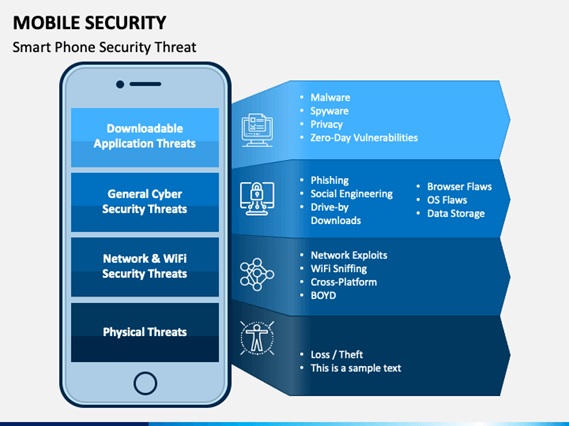
In today's digital landscape, mobile devices have become a prime target for cybercriminals. Understanding the top 5 mobile security threats is essential for safeguarding your personal information and maintaining your privacy. One major threat is malware, which can infiltrate your device through harmful apps or websites. Malicious software can steal sensitive data, track user activity, or even gain control of the device itself. According to recent studies, nearly 50% of mobile device users have experienced some form of malware attack, making it critical to stay informed and adopt preventive measures.
Another significant risk comes from phishing attacks. Cybercriminals often use deceptive emails, text messages, or social media messages that masquerade as legitimate communications to trick users into sharing personal information. Additionally, unsecured Wi-Fi networks present a substantial security vulnerability, allowing hackers to intercept sensitive data as it's transmitted. To enhance your security, always ensure that your device is equipped with the latest software updates and consider using a reliable mobile security application to help protect against these evolving threats.
Counter-Strike is a popular multiplayer first-person shooter that has captivated gamers since its debut in the late 1990s. With strategic gameplay, team cooperation, and a variety of maps and game modes, it has established itself as a competitive staple in the eSports scene. Additionally, players often take steps to protect their devices; for those looking for the best security options, Top 10 iphone privacy screen protectors can enhance privacy while gaming on mobile.
How to Protect Your Smartphone from Hackers: Essential Tips for Users
In today's digital age, smartphones are essential tools that store a wealth of personal information, making them prime targets for hackers. To protect your smartphone from hackers, it's vital to implement a combination of robust security practices. Start by regularly updating your device's operating system and apps; these updates often contain crucial security patches that fix vulnerabilities. Additionally, consider using a strong password or biometric authentication methods, such as fingerprint or facial recognition, to add an extra layer of security to your device.
Another critical step in securing your smartphone is to be cautious with the apps you download. Only install applications from trusted sources, such as the Apple App Store or Google Play Store, and pay attention to the permissions these apps request. Furthermore, consider enabling features like two-factor authentication for your accounts and using a reputable mobile security app to help detect and prevent any malicious activity. By following these essential tips, you can significantly lower your risk of falling victim to a cyber attack.
Is Your Mobile Data Really Safe? The Truth Behind Common Myths
In today’s digital age, the concern over mobile data safety has become increasingly prominent. Many people assume that their personal information is secure simply because they are using a smartphone. However, myths about mobile data safety abound, leading to a false sense of security. For instance, many believe that mobile networks are inherently safer than Wi-Fi connections. While mobile data does have its advantages, such as end-to-end encryption, it is not immune to risks. Cybercriminals often target mobile devices through malicious apps and phishing attacks, which can put your sensitive information at risk.
Another common misconception is that mobile data is fully protected by the device itself. Although smartphones come with various security features—like biometric locks and security settings—these defenses can be bypassed if users neglect basic security practices. Regularly updating your operating system, avoiding suspicious apps, and utilizing a reputable mobile security application are crucial steps to take. To effectively safeguard your data, understanding the lifecycle of mobile threats and adopting a proactive security mindset are essential strategies for minimizing vulnerabilities.